Note: Here I’ll be discussing only the most relevant and most used commands related to users, groups and passwords management. Here is the first part of this tutorial.
Managing Local User Accounts
useradd command
# useradd USERNAME (OR) $ sudo useradd USERNAME
Creates, USERNAME user account. When run without options as above, it sets reasonable defaults for all fields in /etc/passwd file. The default values used by useradd command are listed within files /etc/default/useradd and /etc/login.defs. The useradd command does not set any valid passwords by default, and the user cannot log in until a password is set. Example:
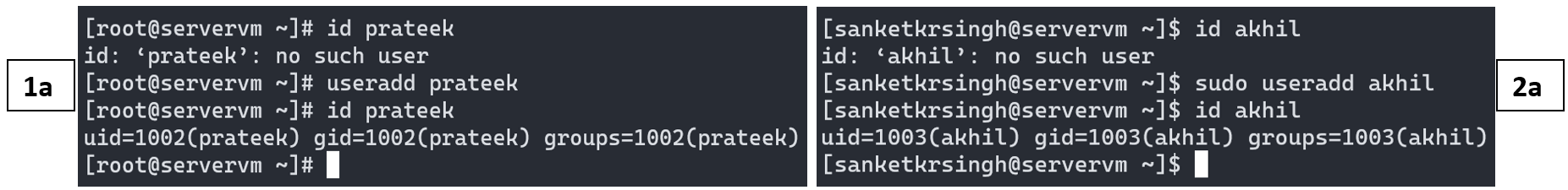
Note: Usually on majority of Linux Distributions, # symbolizes root prompt & $ symbolizes regular/ normal user prompt. Therefore, if a command is preceded by # prompt, that implies root privileges are required for successfully executing the command. As discussed previously, (1a)one may choose to switch to superuser root account or (2a)may escalate privileges via sudo command (if permitted within /etc/sudoers file).
passwd command
# passwd USERNAME (OR) # echo PASSWORD | passwd --stdin USERNAME
passwd commmand is used to set user’s password. Example:
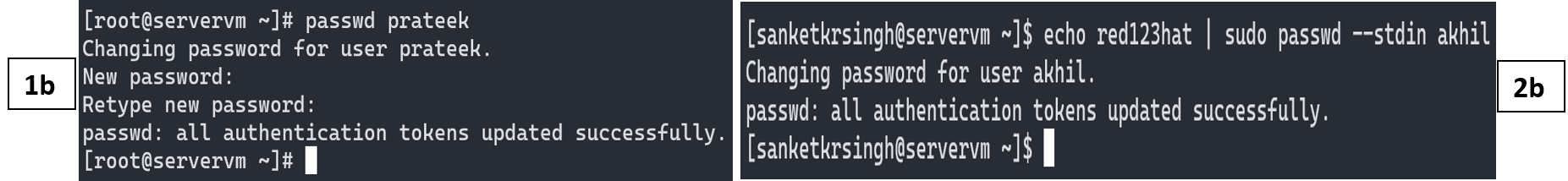
Note: (1b)Former one, displays a prompt for filling in the password and is the recommended way of setting up passwords. (2b)Later one, is meant to be used in shell scripts only and isn’t recommended for interactive shells. Within shell scripts it is used to automate the process of creation (or setting passwords) of one or more users. Not recommended for interactive shells, because it displays password "red123hat" in plaintext form and can be easily be retrieved later using shell’s history command.
userdel command
# userdel -r USERNAME
Deletes, USERNAME user account. Most usual and preferred way of deleting user accounts cleanly. Removes the user private/primary group, entry from file /etc/passwd, /etc/group and /etc/shadow. Files in the user’s home directory will also be removed along with the home directory itself and the user’s mail spool. Files located in other file systems will have to be searched for and deleted manually.
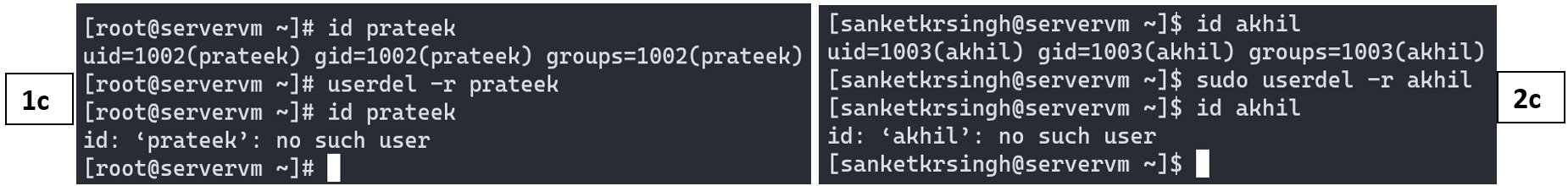
Note: For deleting user account without deleting any files and directories associated with the user, simply use: # userdel USERNAME. Though this method isn’t recommended, because it may generate security issues and information leakage.
When a user is deleted this way, the files that are owned by the user get associated with an unsigned UID and GID number. No valid USERNAME & GROUPNAME remains associated with UID and GID number of the deleted user anymore. Say later on, if the Admin decides to add another user and system chooses to associate this new user with the UID & GID of previously deleted user, this new user will get the ownership of the old user’s remaining files. The image below shows, how the ownership of files held by deleted user anubhav get erratically transferred to new user vikas:
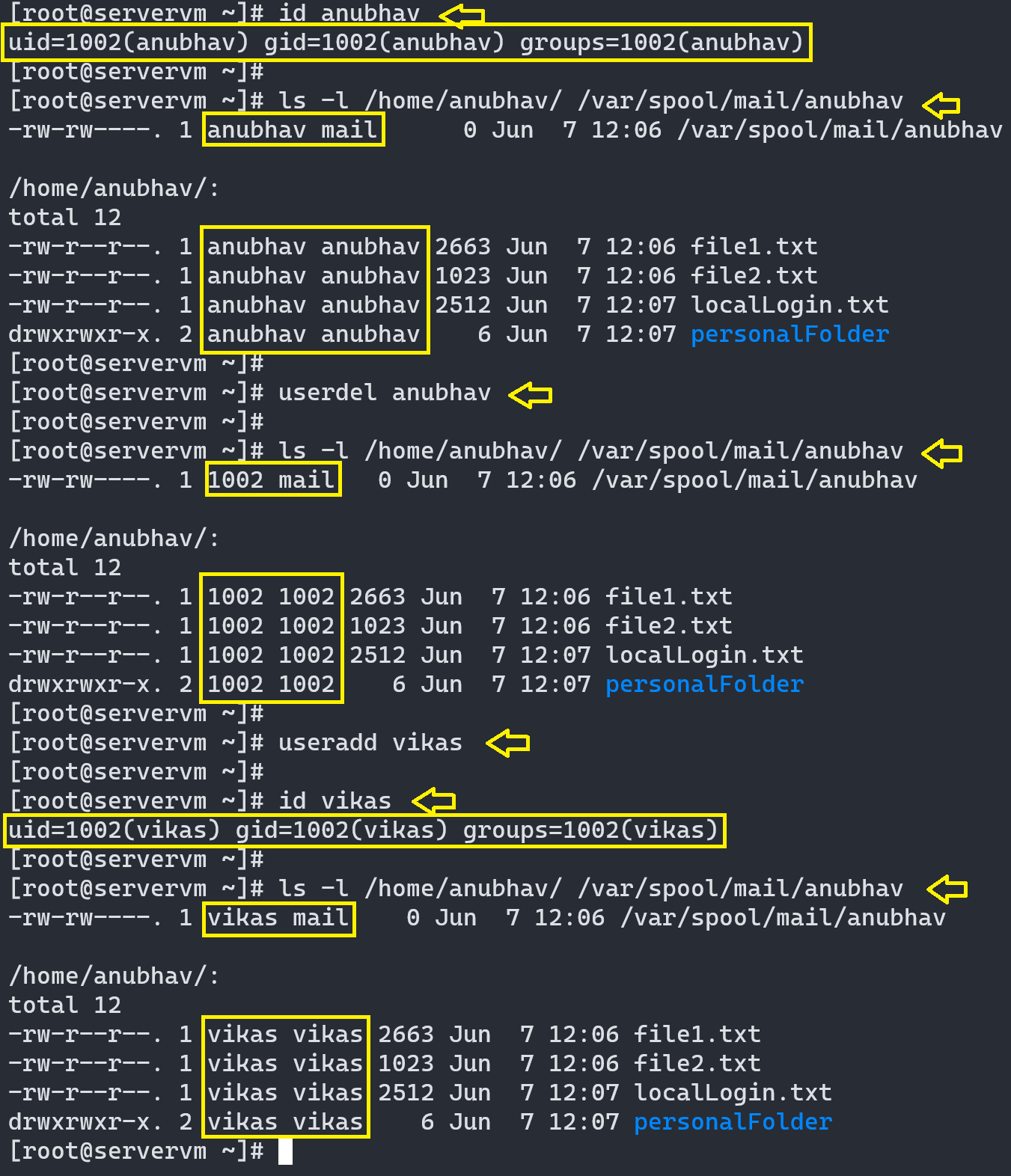
Solution to this problem is to either remove all "unowned" files from the system, when the user that created them is deleted or manually and carefully assign the "unowned" files to a different user. The root user can find "unowned" files and directories by running following command:
# find / -nouser -o -nogroup 2> /dev/null
usermod command
usermod command is used to make changes to already created user accounts. Most of the options used with usermod command can also be used with useradd command while creating a user’s account.
For more details refer to man pages: useradd(8), passwd(1), userdel(8) and usermod(8).
Managing Local Groups
groupadd command
…is generally used for creating supplementary or secondary groups. Because primary groups are automatically created, when the users are created using useradd command.
Note: While using useradd command, user private (or primary) group is created first. Because a group must exist before a user can be added to the group.
# groupadd GROUPNAME (OR) $ sudo groupadd GROUPNAME
Creates GROUPNAME group, and the next available GID from the range specified within file /etc/login.defs (usually 1000+) will be allotted to group GROUPNAME.
Note: Given the automatic creation of user private groups (GID 1000+), it is generally recommended to set aside a range of GID numbers to be used for supplementary groups. Say 5000+ etc.
groupdel command
…is used to remove a group.
# groupdel GROUPNAME (OR) $ sudo groupdel GROUPNAME
Deletes GROUPNAME group.
Note: A group may not be deleted, if it is the primary group of any existing user.
groupmod command
…is used for modifying existing groups definitions.
For more details refer to man pages: groupadd(8), groupdel(8) and groupmod(8).
Managing User Passwords
In past, encrypted passwords were stored in the world-readable /etc/passwd file. This was thought to be reasonably secure until dictionary attacks on encrypted passwords became prevalent. At that point, the encrypted passwords, or password hashes, were moved to the more secure /etc/shadow file. This file, which can only be read by superuser root, also allowed password aging and expiration features to be implemented.
The shadow file stores local users passwords, password aging and expiration information, all organized into nine fields. Following is the format of the shadow file:
USERNAME:PASSWORD:LASTCHANGE:MINIMUM:MAXIMUM:WARNING:INACTIVE:EXPIRE:RESERVED
- USERNAME is a valid username which exists on system.
- PASSWORD is encrypted password. If it starts with an exclamation mark, it implies, that the password is locked, thereby, denying access to the user’s account.
Note: The password field can further be divided into three fields separated by $ symbol: HASHING_ALGORITHM$SALT$ENCRYPTED_HASH, where
- HASHING_ALGORITHM is a single digit unsigned integer value. Value 1 indicates an MD5 hash, 5 indicates SHA-256 hash and number 6 appears when a SHA-512 hash is used. SHA-256 and SHA-512 are considered strong password hashing algorithms. The default algorithm used for password hashes can be changed by superuser root by running the command:
# authconfig --passalgo HASHING_ALGORITHM, where HASHING_ALGORITHM is one from md5, sha256, and sha512. From RHEL7 onwards, RHEL7 and based distributions use SHA-512 hashing algorithm by default. - SALT is a string of random characters, used to encrypt hash. The salt and unencrypted password are combined first and encrypted further to create the encrypted password hash. The use of the salt prevents two users with the same password from having identical entries in the
/etc/shadowfile. - ENCRYPTED_HASH is the combination of salt and unencrypted password, which is encrypted further using the hashing algorithm selected in the first field.
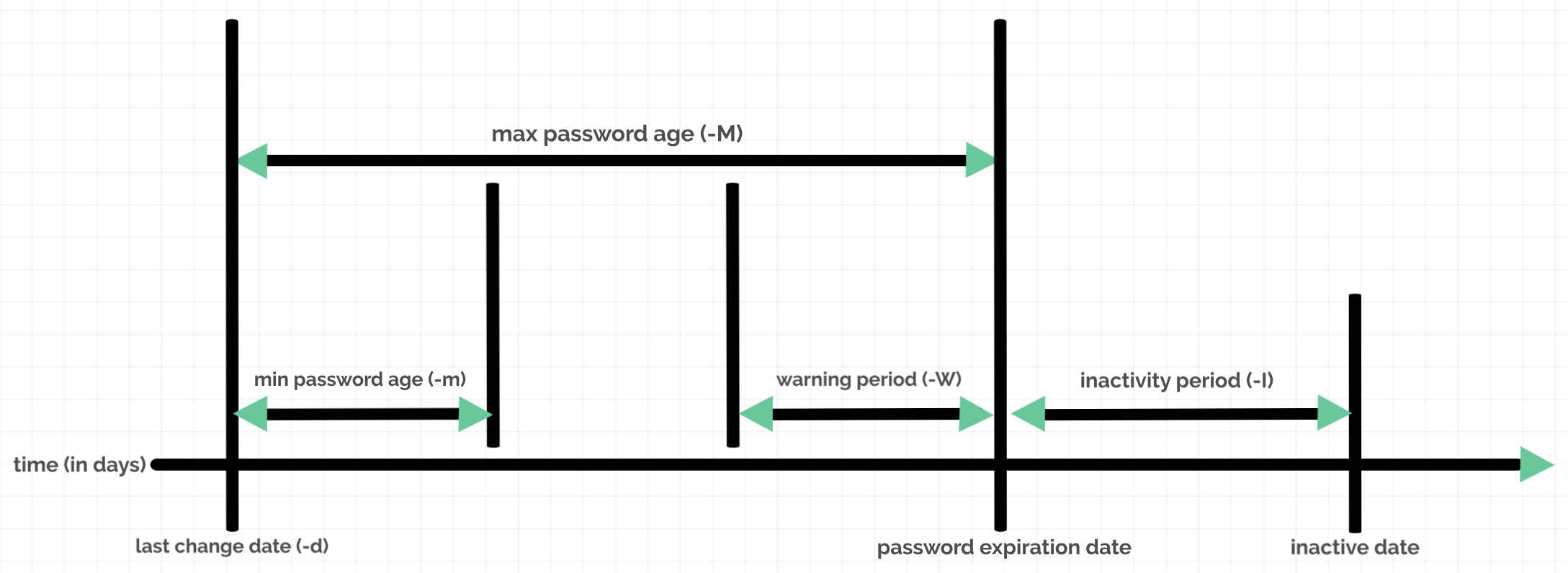
- LASTCHANGE(-d) (LAST CHANGE DATE) field holds the last date when the password of the account was changed. This date is expressed as the number of days since January 1, 1970 (aka UNIX Time or Epoch Time).
Note: Value 0 has a special meaning, it enforces user to change the password during next login attempt. An empty field means that password aging features are disabled. - MINIMUM(-m) (MINIMUM PASSWORD AGE) field is the number of days a user will have to wait before being allowed to change the password again.
Note: An empty field or value 0 means that there is no minimum password age set. - MAXIMUM(-M) (MAXIMUM PASSWORD AGE) field is the number of days after which the user must change the password. Note: An empty field means that there is no maximum password age requirement, no password warning period and no password inactivity period (see below). If maximum password age is lower than minimum password age, the user cannot change its password.
- WARNING(-W) (PASSWORD WARNING PERIOD) is a subset of the MAXIMUM PASSWORD AGE. It is usually the last few days of MAXIMUM PASSWORD AGE. For more clarity look at the image below. It is a soft reminder for a set number of days (warning period), within which, user is asked to change password while logging into the system, failing which, current (or old) password will become inactive or unusable. Though, nothing is enforced and user is allowed to ignore this warning.
Note: An empty field or value 0 mean that there is no password warning period set. - INACTIVE(-I) (PASSWORD INACTIVITY PERIOD) starts, once the warning period (or MAXIMUM PASSWORD AGE) is over. This can be considered as the final warning period within which user is enforced to change the account’s password. User’s current password becomes inactive and login is denied, unless password is changed.
Once inactivity period is elapsed, the password gets expired. Once password gets expired, login is denied and no further option to change password is given to the user. At this stage, user should contact the System Administrator for support.
Note: An empty field means that there are no enforcement of an inactivity period. - EXPIRE(-E) (ACCOUNT EXPIRATION DATE) is the date of expiration of account, expressed as the number of days since January 1, 1970.
Note: Account Expiration differs from the Password Expiration (mentioned above). In case of an account expiration, the user shall not be allowed to login. In case of a password expiration, the user is not allowed to login using the password. An empty field implies that the account will never expire. - RESERVED field is reserved for future use.
The following diagram relates the Password Aging parameters discussed above and can be adjusted using chage command (shown below) to implement password aging policy. Editing the /etc/shadow file directly isn’t recommended, always use standard commands like usermod, passwd, chage and authconfig to make required changes.
#chage -d 0 USERNAME
Force USERNAME user, a password update on next login.
#chage -l USERNAME
List USERNAME user, current settings.
#chage -E YYYY-MM-DD USERNAME
Expires USERNAME account on a specific day. It expires the account and not the password.
Note: The date command can be used to calculate date in the future: $ date -d "+45 days"




